The breaking point that puts an end to all the great features of WordPress, is computer security, because having firm foundations and business technology pillars, we will always question the continuity of the business. And so the phrase is born: WordPress is not safe. This phrase, absent from technical analysis, whose conventional meaning is repeated again and again without alterations, represents a commercial error of great importance, because a good computing professional knows that WordPress is safe, and that the real problem lies in the administration of the CMS and the establishment of protocols through which a website, regardless of the content management system (CMS) used, is always subjected to various and periodic security analyzes. This is what is known in the field of computing security, as the human factor.
On the contrary, the common tendency of a basic or average WordPress user is to look for plugins that secure or scan the CMS inside, usually after they have been hacked, as a result of endless bad practices that, one way or another will lead them to use some type of scanner; on the other hand, there are more sensible and cautious users, those who are looking for analysis services or WordPress vulnerability scanner, in the first instance.
In the commercial path we have the obligation to maintain third party services that help us strengthen our business, especially when the capacity of investment and hiring of human resources in startups, small and medium enterprises, tends to be limited. If you have the opportunity to choose between a ethical hacker or a pentesting company that you cannot pay, a set of plugins that, instead of facilitating the negotiations, sow doubts about which one is the best, reaping just lack of time and seriousness because of their payment configurations and functionalities that are only displayed once these plugins are installed in the CMS, and a WordPress vulnerability scanner service that does everything all at once, your choice, will obviously be a scanner.
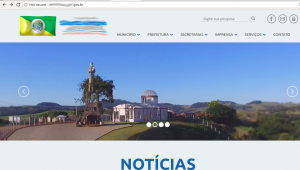
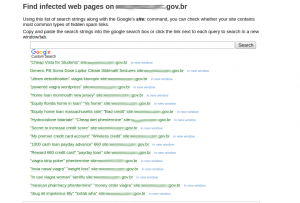
However, what is the level of success of a WordPress malware scanner? The best way to test them is with websites infected by malware, or hacked. For this, I will use a website of brazilian government, infected with spam redirection to itexamoffice.com:
4 WordPress Security Scanners (not) recommended
Shallow Details, Fake Reports & Empty APIs
From the official section for hardening, WordPress.org recommends 4 security scanners:
-
VirusTotal, by Google
-
Sitecheck, by Sucuri
-
Unmaskparasites, by Denis Sinegubko and Sucuri
-
Redleg AW-Snap, by Safe Browsing APIs (Gooogle)
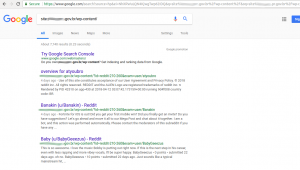
VirusTotal
In VirusTotal the web is listed by phising, although it is only identified, strangely, by 1 of 67 antivirus:
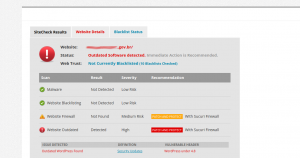
Sitecheck
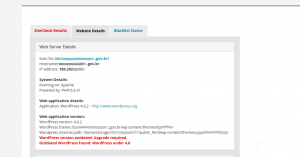
With Sitecheck we warned update alert for the WordPress version, an opportunistic and well done cross selling firewall marketing, and a reference to full path disclosure:
Unmaskparasites
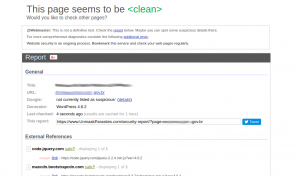
Unmaskparasites plays a role of negligent insecurity, as it delivers reports of clean websites, also deceiving users with reference to infections or non-existent hacking, to finally recommend Sitechek, the scanner described above that does not detect security problems but does makes references to the firewall vending:
Redleg AW-Snap
The last one on the list, AW-Snap, that should inform us of the infection, surprisingly, does not report security alerts:
6 WordPress Vulnerability Scanner Alternatives
Web Mirrors & Useless Information Gathering
The outlook is not good, but thanks to the previous exercise we now have certainty and conviction that we should not trust the results of these WordPress scanners and it is better to try alternatives:
-
WordPress Security Scan, by Hacker Target
-
Wpscans, by Triop AB
-
Wprecon, by Hacker Target
-
WordPress Security Scanner, by WP Loop or First Site Guide
-
WordPress Vulnerability Scanner, by WP Neuron
-
Online WordPress Scan or Scap WP, by Greg Boggs
WordPress Security Scan
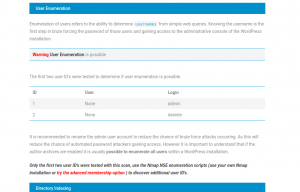
While it is true we can collect general information, the big difference of this scanner versus all the previous ones, is that we finally managed to obtain valuable data on WordPress security, because it listed 2 user names to enter the backend (admin and daniele):
Wpscans
Unfortunately, it is not possible to go deep into this WordPress security scanner, since it offers exactly the same details as Sitechek by Sucuri:
Wprecon
Yes, it is a WordPress Security Scan by Hacker Target clone, therefore, it yields the same results, nothing new:
WordPress Security Scanner
As a scanner of gathering information and detection of HTTPS headers works perfect, but it is absent in the plane of vulnerabilities; although with one exception: jeferson avila user admin was found:
WordPress Vulnerability Scanner
In short, it does not work, every time I tried it, it maintained an infinite loop of scanning:
Online WordPress Scan or Scan WP
Like Unmaskparasites by Sucuri, the scan is superficial, therefore, it is not appropriate:
9 Web Vulnerability and Malware Scanners for WordPress
The Big Leagues: False Positives & King Coronation
What do we do when the recommended security scanners from the official website of WordPress.org do not meet the real needs of analysis for a hacked website, and the most known online scanners for WordPress security do not detect vulnerabilities that are in sight of the human eye?
-
Safe Browsing Site Status, by Google
-
Web Inspector, by Comodo Security Solutions
-
Website Malware Scanning, by Foregenix
-
Rescan, by Revisium
-
Secapps, by Websecurity
-
Web Server Security Test by Hig-Tech Bridge or HT Bridge
-
Acunetix Online, by Acunetix
-
Scan, by Qualys
-
Hackmetrix, by Secsignal Quantum
Safe Browsing Site Status
As we saw with Redleg AW-Snap, this is the base from which the APIs service is provided, consequently, the result is identically null:
Web Inspector
When I hear the Comodo brand, the first thing that comes to mind are SSL certificates, and based on that reputation, it’s surprising that their scanner detects anything:
Website Malware Scanning
Update notification for WordPress version, and absence in security alerts:
Rescan
Site clean:
Secapps
Although they use OWASP Top 10 as a standard, the tendency to detect WordPress updates is repeated:
Web Server Security Test
As with several of the already tested scanners, this online tool is limited to footpring:
Acunetix Online
At first glance, it is a web vulnerability scanner that promises, but requires many hours (days) of scanning and configurations subject to the technical factor of network scan in its platform; your patience will give the game for lost, and with a 99% chance you’ll look for another scanner, just for the time factor:
Scan
With great rapidity of scanning, this online service manages to compete in the major leagues, but loses the game by listing a large number of false positives and vulnerabilities in WordPress that are not accurately identified and cannot be checked and associate to plugins, themes , web services in WordPress or web legacy applications empirically:
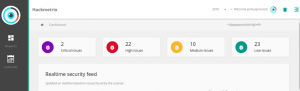
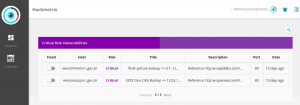
Hackmetrix
Speed, precision, technicality, adaptability and an OWASP Top 10 standard, define the web security scanner that undoubtedly crowns itself as the king. Thanks to its detail feature in the identification of vulnerabilities, it is possible to know with certainty how many and which plugins installed in WordPress incur in known security flaws, delivering reliable and real information:
And as it looks, it is possible scan ISP or host provider:
Hackmetrix found 5 WordPress login usernames, recognized specific failures associated with plugins, and false positives are categorized as low risk vulnerabilities.
But, web security scanners have a common problem: domain verification. If Hackmetrix add this feature, will be the best of the best WordPress Vulnerability Scanner (something more than being the king). Good news: Hackmetrix team it’s working it; in the coming weeks, Hackmetrix will have ownership verification.
WordPress is the CMS par excellence: companies, universities, political and non-profit organizations base their web technology on this content manager. According to the company Buith With, at the date of publication of this article (April 2018), about 20 million websites using WordPress that were scanned by its detection and recognition system, which exceeds the 10 best millions that the company Q Éxito uses as a statistical base in W3 Techs, but the digit is much higher, since it is asserted that more than 60 million people have used the CMS, and that it represents 30% of the global Internet. This marked preference for WordPress is the explanation of its intrinsically versatile, multipurpose and scalable core, which is possible to create from a simple blog, something as useful as a website with shopping cart and bank payment gateway; WordPress delivers ease to create forums, e-learning platforms, and innumerable categories of websites.
What is the best way to ensure that all the features of WordPress are used with fullness and grandeur, while ensuring the continuity of your business? Hackmetrix, the answer.